Need Connectivity? Chat With a Solutions Architect Today.
- Solutions
Evolve Your Network
Managed Connectivity Solutions
Data Center & Colocation
Cloud Solutions
Private Networking Solutions
SD-WAN Connectivity
Solutions Brief
- Partners
Partner with a Proven Leader
Partner With Massive
Contact Our Team
Partner Portal
- Resources
Grow Your Knowledge
Learn About Our Solutions
Read More on Our Blog
- About
Who is Massive Networks
About Massive Networks
Contact Our Team
Your Global Connectivity Fabric
Reliability
Worry Less about your network performance and connectivity
Security
Your security questions answered without trade-offs or compromise.
Simplicity
Your global connectivity network designed by engineers like you.
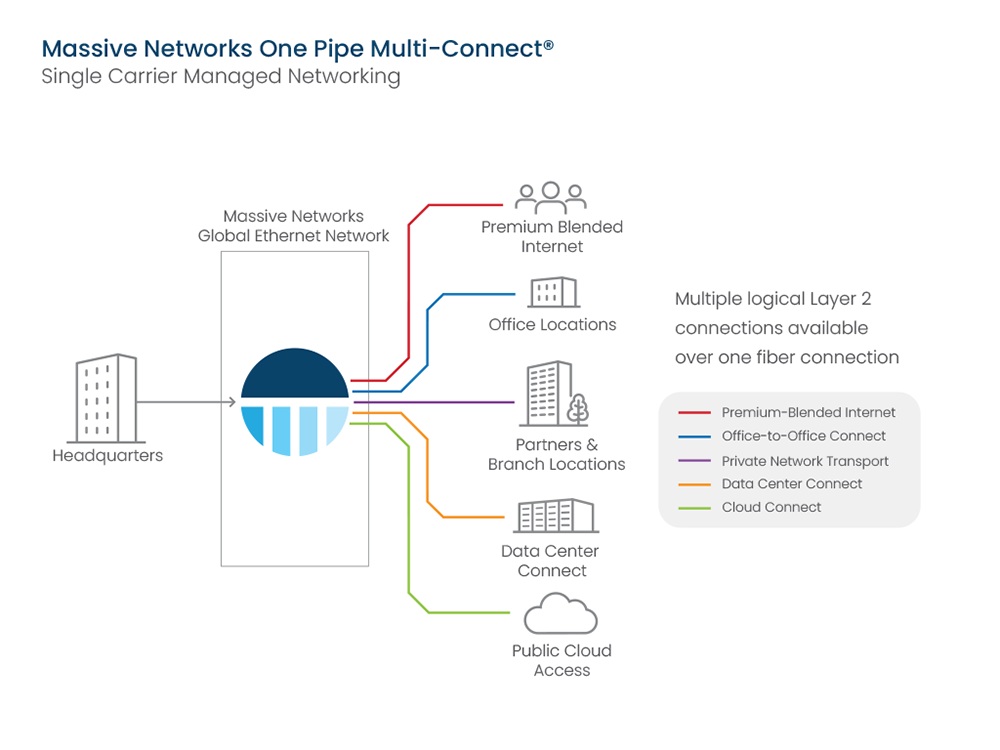
One Pipe Multi-Connect
Your One Pipe makes managing multiple circuits and carriers a thing of the past. One Pipe delivers a fully customizable set of connections to the resources around the globe that support your business. With One Pipe you enable the delivery of multiple segregated data streams through a single redundant connection. One Pipe is the core of the simplicity, security, and reliability Massive delivers in support of your business. Say goodbye to siloed last-mile connections, complex network hand-offs, and multiple carriers to manage.
Your Global Ethernet Network

Your business relies on a multitude of global connections to offices, data centers, clouds, and SaaS services. Your One Pipe connection delivers those connections simply, securely, and reliably across a network of 60+ million-lit buildings, 450+ clouds, and 6,000+ data centers. One Pipe eliminates the complexity of managing multiple carriers without trade-offs. One carrier, one MSA, one invoice, and one US based support team available 24/7/365.
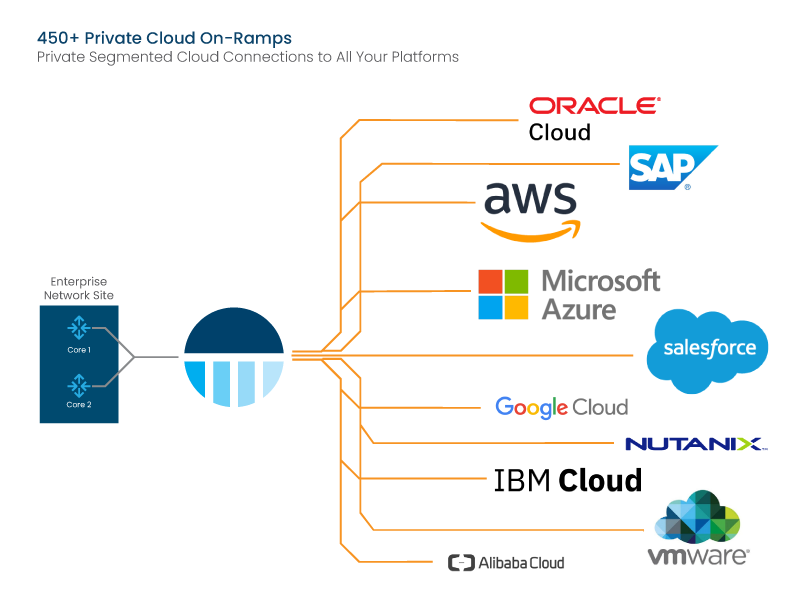
Elevate Your Cloud
Empower your network operations with our next-gen Private Cloud On-Ramps. Evolve user experience by seamlessly connecting to major cloud and SaaS platforms through segmented private data streams, ensuring increased privacy and enhanced security. With a focus on performance optimization and flexibility, our solution offers increased speed, efficiency and scalability enabling operators to deliver superior connectivity to their users. Experience the power of streamlined cloud connectivity and elevated performance in an integrated single circuit solution.
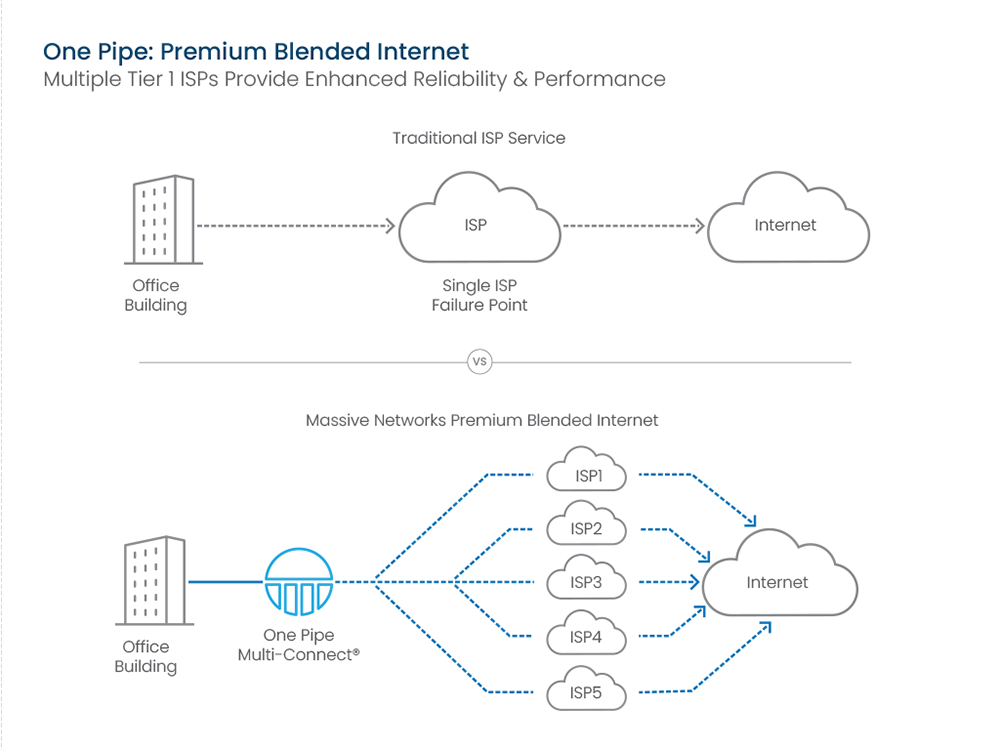
Speed of Light Access
Finally a solution that brings high-performance Tier 1 data center bandwidth right down to all your locations. With Premium Blended Internet, your internet services are powered by a combination of up to five Tier 1 Internet Service Providers (ISPs). This ensures continuous support for your critical workloads even if one provider fails your traffic is instantly routed over the best possible path. When it comes to Internet Access, redundancy is the name of the game, and Premium Blended Internet is your MVP.
How Can You Evolve Your Network?
Dependable Connectivity

Connecting to Massive’s Premium Blended Internet provides you connectivity from up to 5 Tier 1 ISPs. Deliver Tier 1 data center quality internet options to any One Pipe capable site.
Redundant ConnectivityProven Technology

Your One Pipe connection is built on a global Ethernet network using reliable Layer 2 Ethernet connections. Connectivity that’s been demonstrated to have high performance and consistent operation over decades of deployment.
Proven TechnologyDedicated Support

When problems arise, your operators need answers and solutions fast. Massive Network’s highly trained, dedicated, US-based network engineers monitor and manage your carrier connections 24/7/365, ensuring those answers and solutions are a phone call away.
Trusted SupportReduce Your Attack Surface

Your One Pipe reduces your attack surface by eliminating reliance on internet links for sensitive traffic. This eliminates or reduces the need for complex VPNs decreasing complexity while increasing network visibility and observability.
Shift My WorkloadsSecurely Connect Branch Offices

It’s time to move your office-to-office connections off of internet links to consistently reliable and secure private connections. Using One Pipe you connect your offices globally with private, segmented, and secure links. Learn how Massive supports your shift from complex VPN based internet links to private circuits while increasing visibility, security, and simplicity.
Connect My OfficesA Truly Global Ethernet Network

Connect across 58+ countries to 60+ million lit buildings, 450 clouds, and over 6000 data centers. Increase your access to regional clouds, satellite offices, and data centers at strategic locations worldwide.
Going GlobalFree Your Company from Vendor Sprawl

Managing multiple carriers is a distraction to running your business and delivering WAN connectivity. Massive Network’s eliminates the distractions, delivering all for your global connectivity needs with one carrier, one MSA, one support team, and one invoice from one Carrier Evolved.
Reduce Vendor SprawlSimplify Your Enterprise's Network Architecture

Your Multi-Connect suite of solutions delivers fundamental network efficiencies. Efficiencies that impact your entire organization. From reduced reliance on SD-WAN and VPN solutions, to eliminating the need for MPLS, Massive lets you reduce modern network complexity, and the fragility and operational cost that comes with it.
Simplified Networking
A Single Global Network

Why choose a separate carrier for each of your diverse connectivity requirements? With One Pipe Multi-Connect(R) all of your internet, cloud, SaaS, office, and data center connectivity needs are delivered securely segmented from one carrier on One Pipe.
Single Carrier SolutionIs My Site Ready for Carrier Evolved?
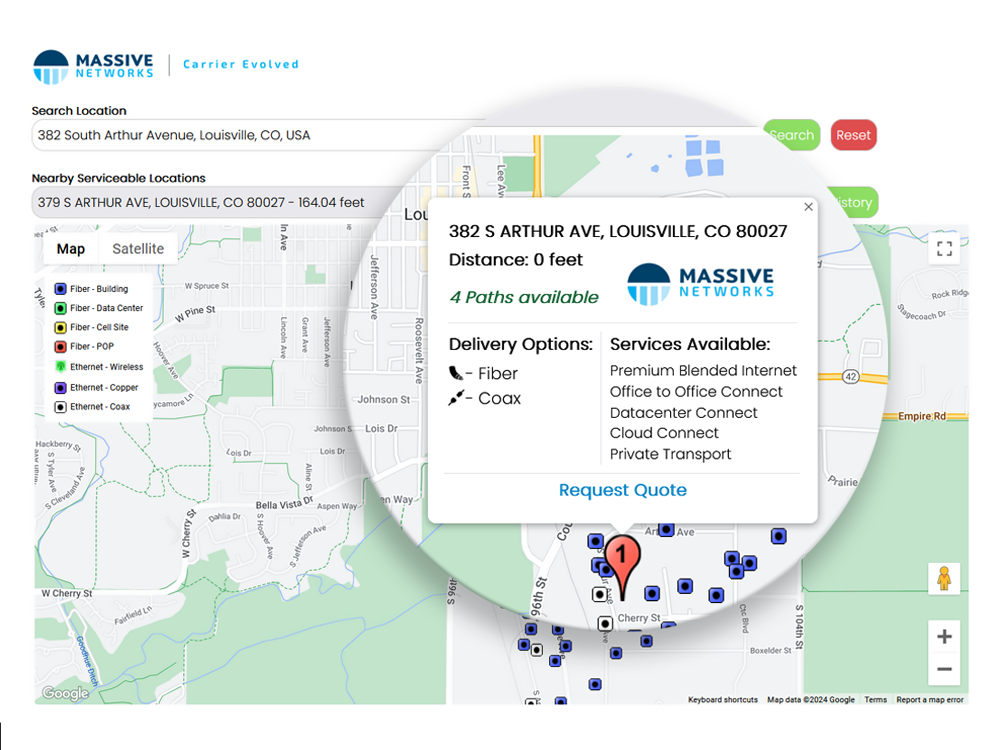
With over 60+ Million Fiber-Lit Buildings Across 58+ Countries Worldwide, the answer is probably yes! Stop wasting time tracking down building managers or contacting carriers to see if they have services at your locations. Identify what connectivity options are available for millions of buildings across the globe in seconds FOR FREE. Find your fiber and get a quote on services for all your locations and simplify your network in less than half the time.

Why Massive Networks
Choosing Massive Networks means partnering with a global leader in enterprise connectivity solutions. Our dynamic Carrier grade services have been designed to enable enterprise agility, transforming your network into a powerhouse of growth and innovation. Our simplified approach resolves multi-carrier complexity with a single global carrier network delivering high performance and reliable last mile to last mile service. With Massive Networks, your network connectivity becomes a strategic asset.